Deploy with CloudFormation and Operation Verification
This document describes how to deploy sample code from this catalog using AWS CloudFormation and perform operation verification. We will deploy resources to AWS using AWS CloudFormation.
Deployment Configuration
Deployment Procedure
1. Verify IAM Role and Permissions Used for Deployment
Please verify the permissions of the instance role assigned to the instance created with AMI. The recommended approach is to execute with Administrator permissions first, then use AWS IAM Access Analyzer to narrow down and apply the necessary permissions.
- For details on AWS IAM Access Analyzer, please refer to the relevant official documentation.
2. VPC Deployment
First, execute CloudFormation deployment using aws-cli to deploy VPC. After executing the command, wait for deployment success from AWS Management Console. Please enter your preferred values for --stack-name, AppName, and EnvName according to your environment
[ec2-user ~]aws cloudformation create-stack \
--region us-east-1 \
--stack-name vpc \
--template-body file://deploy/cloudformation/vpc.yaml \
--parameters \
ParameterKey=AppName,ParameterValue=myapp \
ParameterKey=EnvName,ParameterValue=dev \
--capabilities CAPABILITY_NAMED_IAM
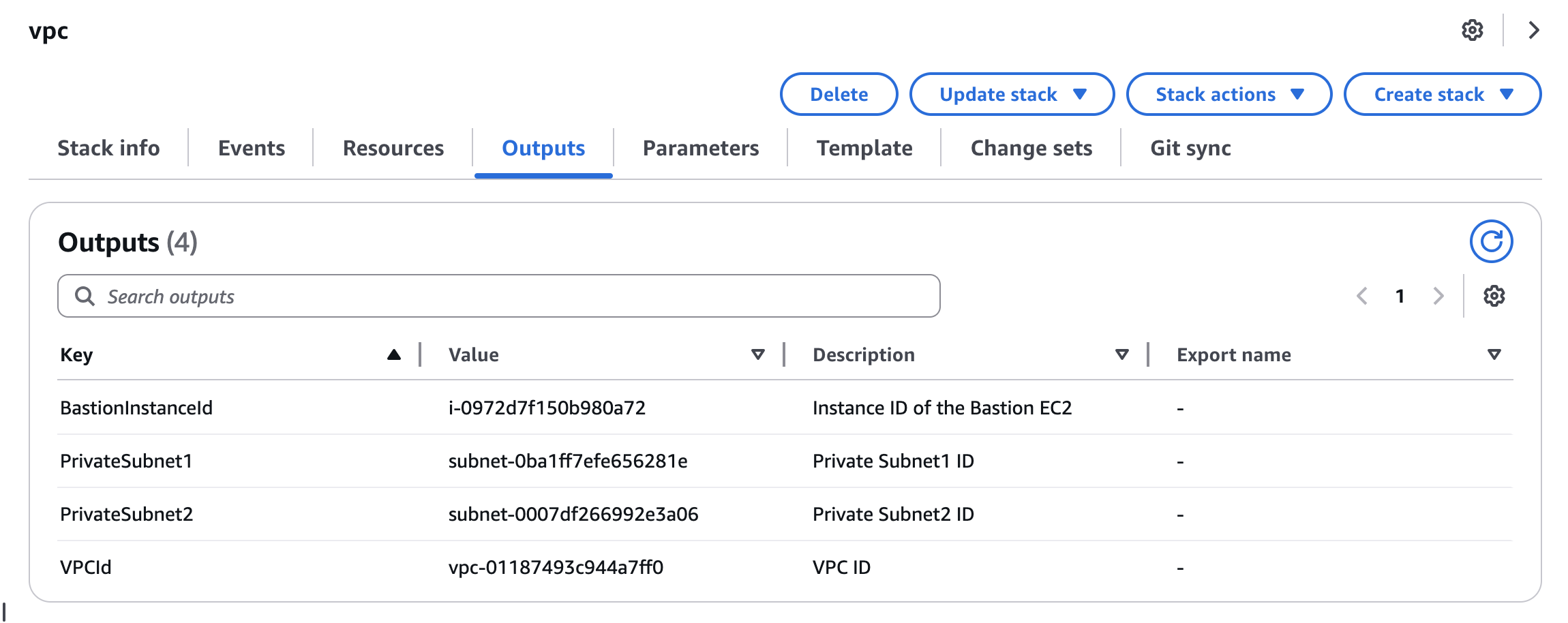
After deployment completion, open the output tab in Management Console and check the following values. These values will be used in subsequent stack deployments.
3. Database Deployment
Deploy Amazon Aurora PostgreSQL within the VPC deployed earlier.
[ec2-user ~]aws cloudformation create-stack \
--region us-east-1 \
--stack-name db \
--template-body file://deploy/cloudformation/db.yaml \
--parameters \
ParameterKey=AppName,ParameterValue=myapp \
ParameterKey=EnvName,ParameterValue=dev \
ParameterKey=DBUserName,ParameterValue=postgreAdmin \ # Enter your preferred value
ParameterKey=DBUserPassword,ParameterValue=SuperSecurePass123 \ # Enter your preferred value of 8 characters or more
ParameterKey=VpcId,ParameterValue=vpc-01187493c944a7ff0 \ # Enter the value from VPC output tab
ParameterKey=PrivateSubnet1,ParameterValue=subnet-0ba1ff7efe656281e \ # Enter the value from VPC output tab
ParameterKey=PrivateSubnet2,ParameterValue=subnet-0007df266992e3a06 \ # Enter the value from VPC output tab
--capabilities CAPABILITY_NAMED_IAM
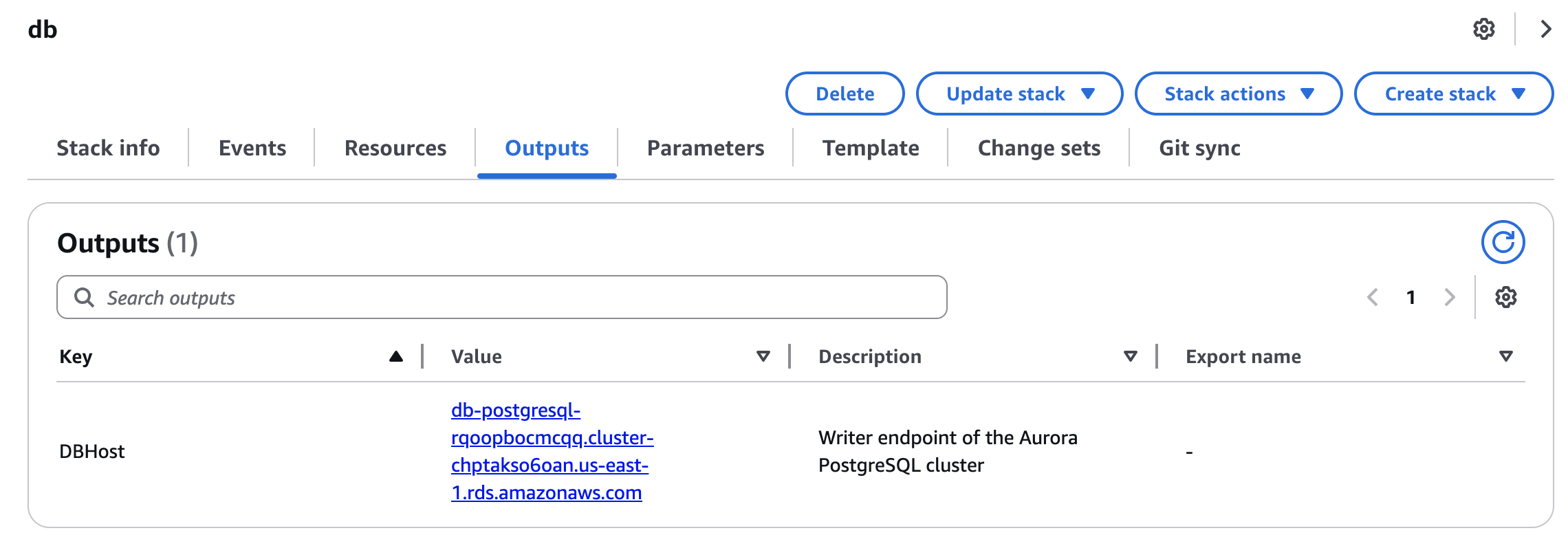
After DB deployment is complete, check the Aurora cluster writer instance endpoint from the output tab in Management Console.
4. Deploy API Gateway + Lambda CloudFormation Stack
Similarly, deploy the stack using aws-cli.
[ec2-user ~]aws cloudformation create-stack \
--regio us-east-1 \
--stack-name apigateway-lambda \
--template-body file://deploy/cloudformation/apigateway-lambda.yaml \
--capabilities CAPABILITY_NAMED_IAM \
--parameters \
ParameterKey=AppName,ParameterValue=myapp \
ParameterKey=EnvName,ParameterValue=dev \
ParameterKey=VpcId,ParameterValue=vpc-01187493c944a7ff0 \
ParameterKey=PrivateSubnet1,ParameterValue=subnet-0ba1ff7efe656281e \
ParameterKey=PrivateSubnet2,ParameterValue=subnet-0007df266992e3a06 \
ParameterKey=S3SourceCodeBucket,ParameterValue=$BUCKET_NAME \
ParameterKey=S3SourceCodeKey,ParameterValue=api.zip \
ParameterKey=DbHost,ParameterValue=db-postgresql-rqoopbocmcqq.cluster-chptakso6oan.us-east-1.rds.amazonaws.com \ # Aurora cluster writer instance endpoint
ParameterKey=DbUser,ParameterValue=postgreAdmin \
ParameterKey=DbPassword,ParameterValue=SuperSecurePass123 \
ParameterKey=DbName,ParameterValue=mydb \
ParameterKey=AppLayerArn,ParameterValue=arn:aws:lambda:us-east-1:<Account ID>:layer:python-lambda-application-template-lib-layer:1 \ # Specify the ARN of python-lambda-application-template-lib-layer noted during package creation
ParameterKey=Psycopg3LayerArn,ParameterValue=arn:aws:lambda:us-east-1:<Account ID>:layer:psycopg3-layer:1 # Specify the ARN of psycopg3-layer noted during package creation
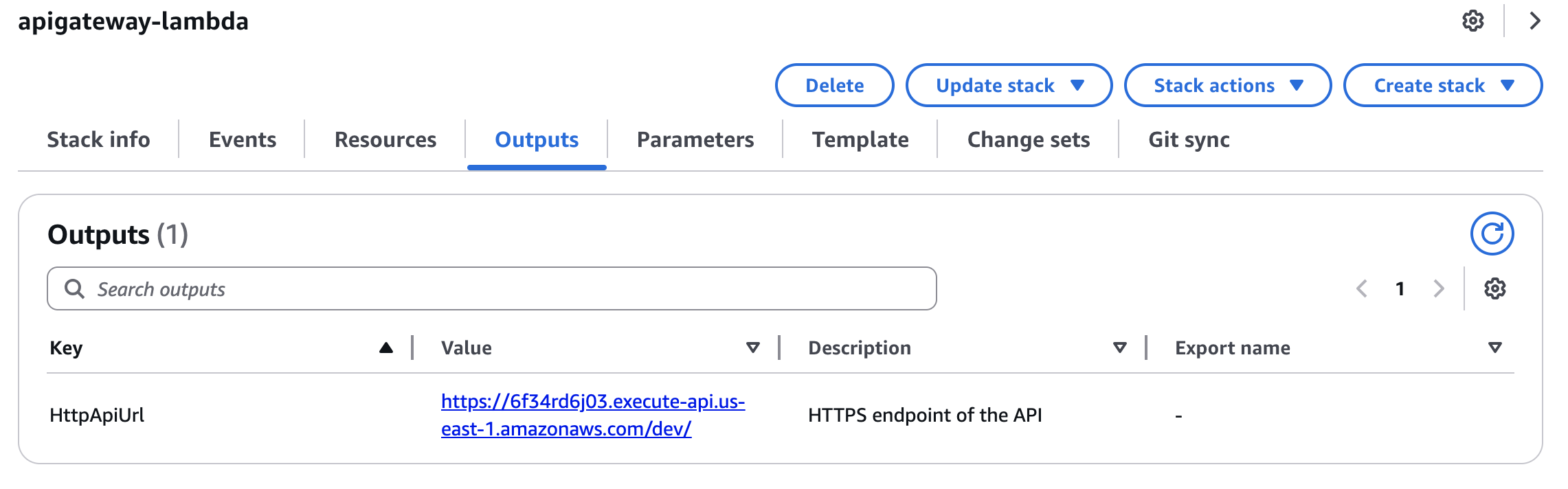
When deployment succeeds, the API endpoint will be displayed in the output tab. Let's use this to perform operation verification.
5. Deploy S3 Event + Lambda CloudFormation Stack
[ec2-user ~]aws cloudformation create-stack \
--region us-east-1 \
--stack-name s3-lambda \
--template-body file://deploy/cloudformation/s3-lambda.yaml \
--capabilities CAPABILITY_NAMED_IAM \
--parameters \
ParameterKey=AppName,ParameterValue=myapp \
ParameterKey=EnvName,ParameterValue=dev \
ParameterKey=VpcId,ParameterValue=vpc-01187493c944a7ff0 \
ParameterKey=PrivateSubnet1,ParameterValue=subnet-0ba1ff7efe656281e \
ParameterKey=PrivateSubnet2,ParameterValue=subnet-0007df266992e3a06 \
ParameterKey=S3SourceCodeBucket,ParameterValue=$BUCKET_NAME \
ParameterKey=S3SourceCodeKey,ParameterValue=event.zip \
ParameterKey=DbHost,ParameterValue=db-postgresql-rqoopbocmcqq.cluster-chptakso6oan.us-east-1.rds.amazonaws.com \
ParameterKey=DbUser,ParameterValue=postgreAdmin \
ParameterKey=DbPassword,ParameterValue=SuperSecurePass123 \
ParameterKey=DbName,ParameterValue=mydb \
ParameterKey=AppLayerArn,ParameterValue=arn:aws:lambda:us-east-1:<アカウントID>:layer:python-lambda-application-template-lib-layer:1 \
ParameterKey=Psycopg3LayerArn,ParameterValue=arn:aws:lambda:ap-northeast-1:<アカウントID>:layer:psycopg3-layer:1
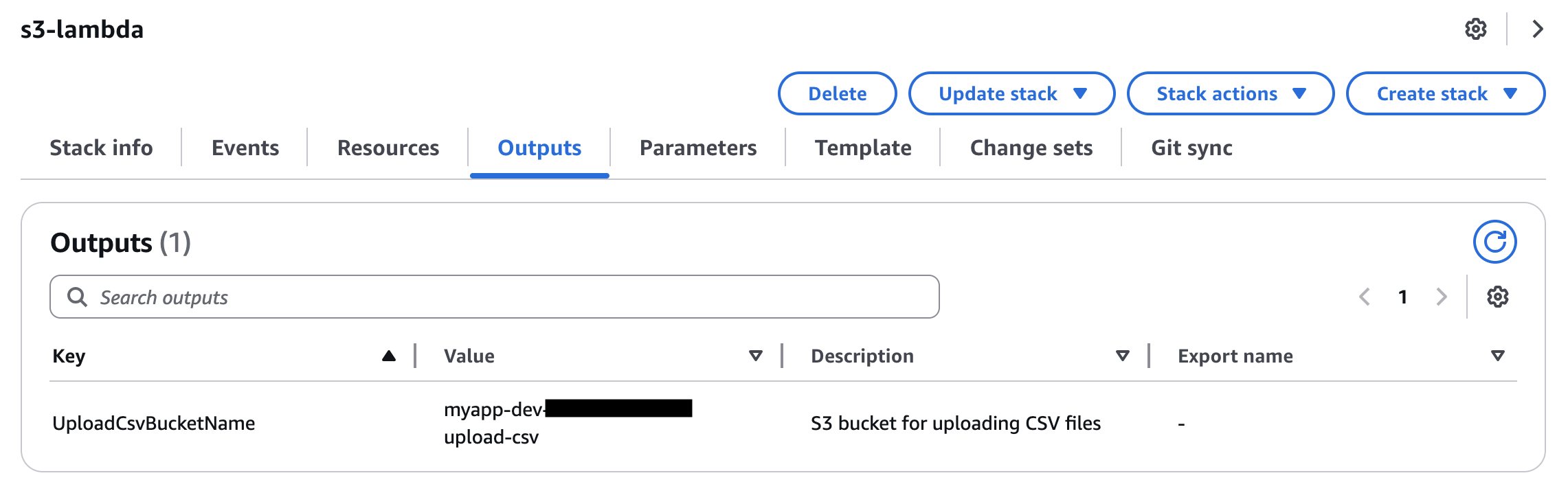
When deployment succeeds, an S3 bucket that triggers events will be created. When you upload user data CSV files here, Lambda functions will start and data will be created in the DB.
Operation Verification
Great work! You can perform operation verification from this page.